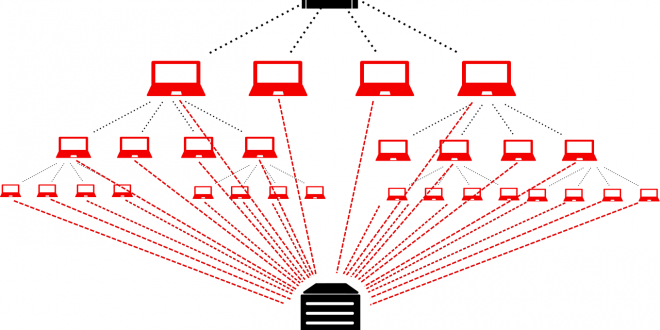
What is a DDoS attack?
Distributed Denial of Service, also known as DDoS, is a form of attack which attempts in making an online service unavailable by overwhelming it with directed traffic from several different sources.
A DDoS attack targets anything and everything with value, from a wide range of important resources that include banks to news websites to healthcare and even your favorite computer games. Practically nothing is discriminated against.
And to make matters worse, DDoS attacks are major. They create huge issues for people regarding publishing and accessing important information, but they are also huge security risks as well. DDoS attacks are a means for hackers to gain notoriety, seeking financial rewards or creating chaos when state-sponsored groups use it as a form of political cyberattack.

Types of DDoS attacks
Just like a DDoS attack targets different platforms and websites, the attacks come in various different forms. However, there are 4 common categories of DDoS attacks in particular that we should emphasize on. Read below to find out:
- Application attacks
This form of attack targets applications by attempting to overwhelm a particular aspect of either an application, service, or software. These are often hard to find and eradicate, as they’re even effective with a small number of attacking machines which generate a low traffic rate.
- Fragmentation attacks
Targeted at pieces of packets (when a datagram [which is a unit of transfer associated with networking] is divided into smaller chunks of information), this form of attack enlists a supply of TCP (which handle packet re-ordering) or UDP (which preserve message boundaries) fragments to a user (now victim) which then overwhelms the victim’s performance, drastically reducing it, and causing them to reassemble the streams.
- TCP Connection attacks
These attacks occupy connections. Most notably, all available connections to an infrastructure’s devices are used. Such devices include application servers, firewalls, and load-balancers. And the scary thing is is that TCP connection attacks are capable of taking down devices with the capability of maintaining their state on millions of connections.
- Volumetric attacks
This form of attack uses up a bandwidth’s entirety, pursuing to overall consume a bandwidth by one of two ways: within the target network or service or within the target network or service and its relationship with the rest of the Internet. Just as the names prescribes, “volumetric” is simply code for congestion—that is what these attacks supremely are.
Similar to the 4 common categories of DDoS attacks, there are only 2 ways DDoS attacks can actually multiply and send traffic.
- Chargen Reflection
With how fast the technological world advances, it’s a surprise to many that many computers and Internet-connected printers support this dinosaur-era testing service named Chargen. Initially, it was meant to allow a user to use a device to respond with a statement of random characters. Now, Chargen is used in a way that is considered an amplified reflection attack, which basically means DDoS attacks that exploit the connectionless nature of UDPs with spoofed requests, thereby disrupting open Internet servers.
- DNS Reflection
Small but mighty—this is what these attacks are. By sending small requests to a DNS server, after forging a user’s IP address, the attacker asks for the DNS server to send the user a large reply. Ensuing after, the attacker is then able to have every single request from its botnet boosted to as big as 70x in size. This, unfortunately, makes it all the more easy for the attacker to overwhelm and hurt the user.

How does a DDoS attack work?
Most often, DDoS attacks work by botnets. And to make matters clear, a botnet is a big group of Internet-connected computers that builds off of one another, each running one or more bots. These computers simultaneously spam a website with data requests and/or your service provider, stealing data, sending spam, and giving the hacker access to the device and its connection.
By the way, DDoS attacks have a heavy reliance on a large proportion of computers in the botnet in order to get what they bargained for. The best way to do this is by leveraging exploits. And it all comes down to how quick, easy, and inexpensive it is to get control of what they want.
In a DDoS attack, a botnet is used by this outline:
- In order to create a botnet, an attacker uses unpatched vulnerabilities, flaws, or malware to install Command and Control, or C2, software on a user’s systems.
- When the botnet is all said and done, the attacker then follows by sending the start command. This command is sent to all of the botnet nodes.
- After, programmed requests are sent to the target server by the botnet.
- If the attack is able to go beyond the reach of the target server’s outer defenses (such as your network’s firewall), the botnet is able to overwhelm most any system quickly.
- What happens after is typically resulted in the form of service outages or, worse yet, entirely crashes the server.
- At the end of it all, the botnet effectively ends the attack by way of productivity loss or service interruption.
The end… That’s not such a happy ending, is it?

Yet DDoS still happen!
DDoS attacks are rapidly evolving, increasingly become more destructive to the Internet and online businesses as the days go by.
They’ve hit some of the most adored and beloved websites on the Internet including Wikipedia and World of Warcraft in September this year. Last year, Fortnite was affected when it had a server issue and ultimate server crash. Heck, in 2017, even DDoS attacks “are increasing in frequency on the healthcare industry,”
These attacks are increasing in frequency. It’s time you suit up.
How to Combat DDoS Attacks
You have to be smart, and you must choose the right defense strategy.
To start, a comprehensive DDoS defense strategy includes recognizing DDoS attack signals right off the bat. You must be able to recognize them early, and so investing in the right technology, expertise, and training can effectively help you in doing so. Cloudflare can help your website withstand DDoS attacks, and is offered by most domain registrars, like 101domain.
Next, you must home in on incident response planning, meaning you’ll have an optimal incident response program at hand and included in your DDoS mitigation plan.
If your website is under a DDoS attack, contact your ISP provider. You can do this by looking up your ISP here. Make sure to ask them whether there is an Internet service outage in your area, if any Internet settings have changed, or if there has been any other network service changes. It’s important to note that DDoS attacks are known to affect ISP providers. Your ISP provider can detect DDoS attacks and thereby re-route your website’s traffic so you won’t have to call for help when it happens (hopefully not.)
Also, you should have your threat intel ready, and you should know what to look for. Some key clues for a DDoS attack are when an IP address makes x amount of requests over y seconds, your server responds with a 503 issue because of service outages, the TTL (time to live) request times out, if using the same connection for internal software and others notice slowness issues beyond your own, or even log analysis solutions show a dramatically unusual spike in traffic.
In order to understand the source of DDoS attacks, join your local ISAC (Information Sharing and Analysis Center) through the CIS (Center for Internet Security) website (which is always free and voluntary to become a member) in order to help gather and share information on cyber threats to critical infrastructure, or use a threat intel service provider such as Dyn (a major DNS provider.)
Additionally, you can use other mitigation defenses and tools: load balancers, which balance web traffic across multiple servers within a defined network thus creating greater network availability, or a cloud-based anti-DDoS solution which filters and/or diverts malicious and unwanted DDoS traffic.
And if you don’t want to have someone do it for you, you can prevent DDoS attacks yourself with careful planning and security measures. You have to have the right tools for preventing these attacks, and Cloudflare is an easy solution. Cloudflare’s advantage is that it combines multiple DDoS mitigation techniques into one solution, making it optimal for the user.
Now that you know…
They’re a very real and costly negative expenditure that can only hurt you and your business.
With how rapidly the Internet and technology is always changing, DDoS attacks have gotten bigger and even worse.
Don’t wait around. You need to be prepared because DDoS attacks are no joke.
 Comeau Computing Tech Magazine 2024
Comeau Computing Tech Magazine 2024